Scaling Identity: Inside the Engineering Marvel of India's Aadhaar System
Think 99.99% accuracy is enough? Not when you’re building a digital ID for over a billion people. Dive into the wild challenges, clever solutions, and massive impact of Aadhaar—India’s audacious quest to give everyone a secure, scalable identity in a country where scale changes everything.

When 99.99% Accuracy Just Isn't Good Enough
I remember sitting in a dingy computer lab during my second year of college, watching my professor beam with pride. We had just hit 99.99% accuracy on our fingerprint detection algorithm. Everyone was cheering, high-fiving, and planning celebratory drinks at the campus canteen.
Except for one visiting scientist from UIDAI (Unique Identification Authority of India), who sat quietly in the corner, looking somewhat unimpressed.
"That's excellent work," he said, choosing his words carefully. "But do you understand what 99.99% accuracy means when you're identifying 1.5 billion people?"
That's 150,000 incorrect identifications. 150,000 people who might be denied services, benefits, or rights because our "excellent" algorithm got it wrong.
"For Aadhaar," he continued, "we need at least 99.999% accuracy. And even that leaves 15,000 errors. That's why we use multiple biometrics, deduplication engines, and constant refinement."
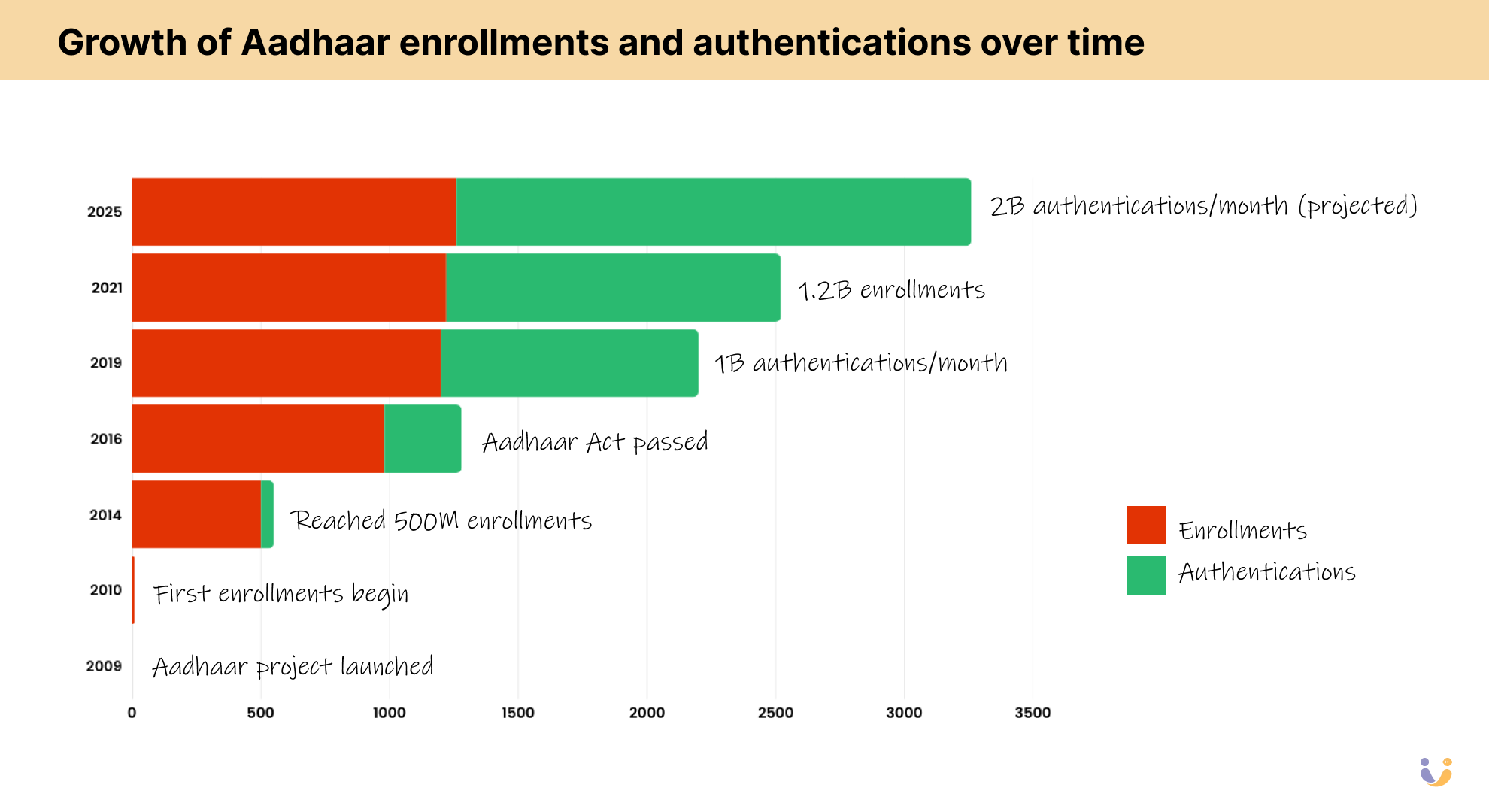
That was my first glimpse into the scale of what India was attempting to build with Aadhaar — the world's largest biometric ID system that would eventually enroll more than 1.3 billion people, creating digital identities for nearly one-sixth of humanity.
The Problem: Identifying a Subcontinent
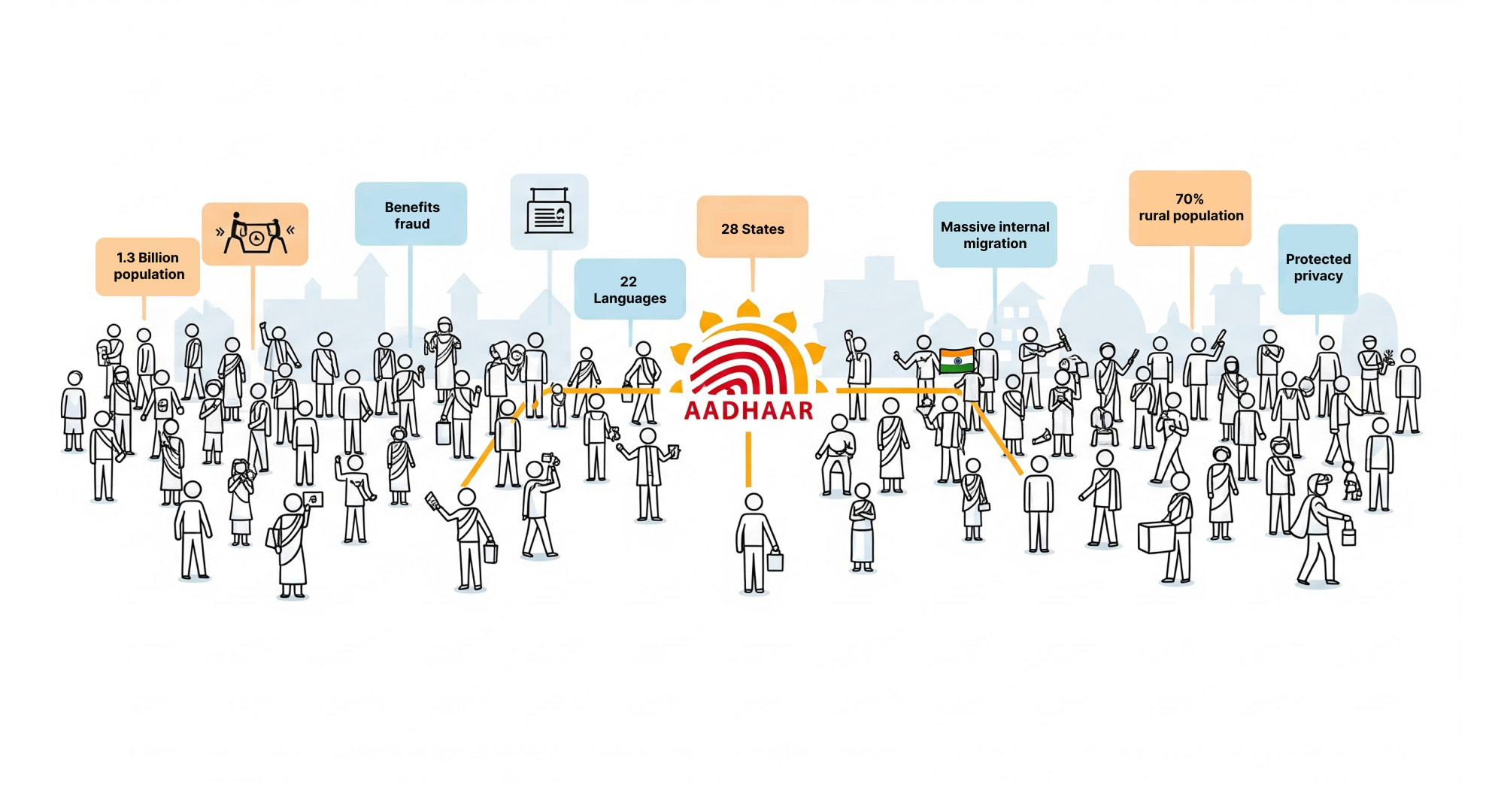
Before we dive into the technical architecture, let's understand the sheer audacity of the problem Aadhaar was trying to solve.
India, a country with:
- 1.3+ billion people (scaling to 1.5 billion)
- 22 official languages
- 28 states and 8 union territories with different infrastructure levels
- 70% rural population often with limited connectivity
- No unified identity system (hundreds of millions without ANY government ID)
- Rampant benefits fraud costing billions annually
- Massive internal migration making tracking nearly impossible
The goal? Give each resident a unique, verifiable, digital identity that:
- could be authenticated anywhere, even with poor connectivity,
- couldn't be duplicated or forged,
- worked regardless of language, literacy, or technical skill,
- could integrate with both government and private systems,
- protected privacy while enabling authentication, and
- scaled to handle billions of authentications daily.
Building Identity at Planetary Scale
The core of Aadhaar's technical architecture revolves around three critical components:
- Enrollment System - Capturing and processing biometrics
- Central Identities Data Repository (CIDR) - Storing and managing the data
- Authentication System - Verifying identities in real-time
Let's break down each one and see how they tackled the scale challenges.
Enrollment: The Pipeline of Unprecedented Scale
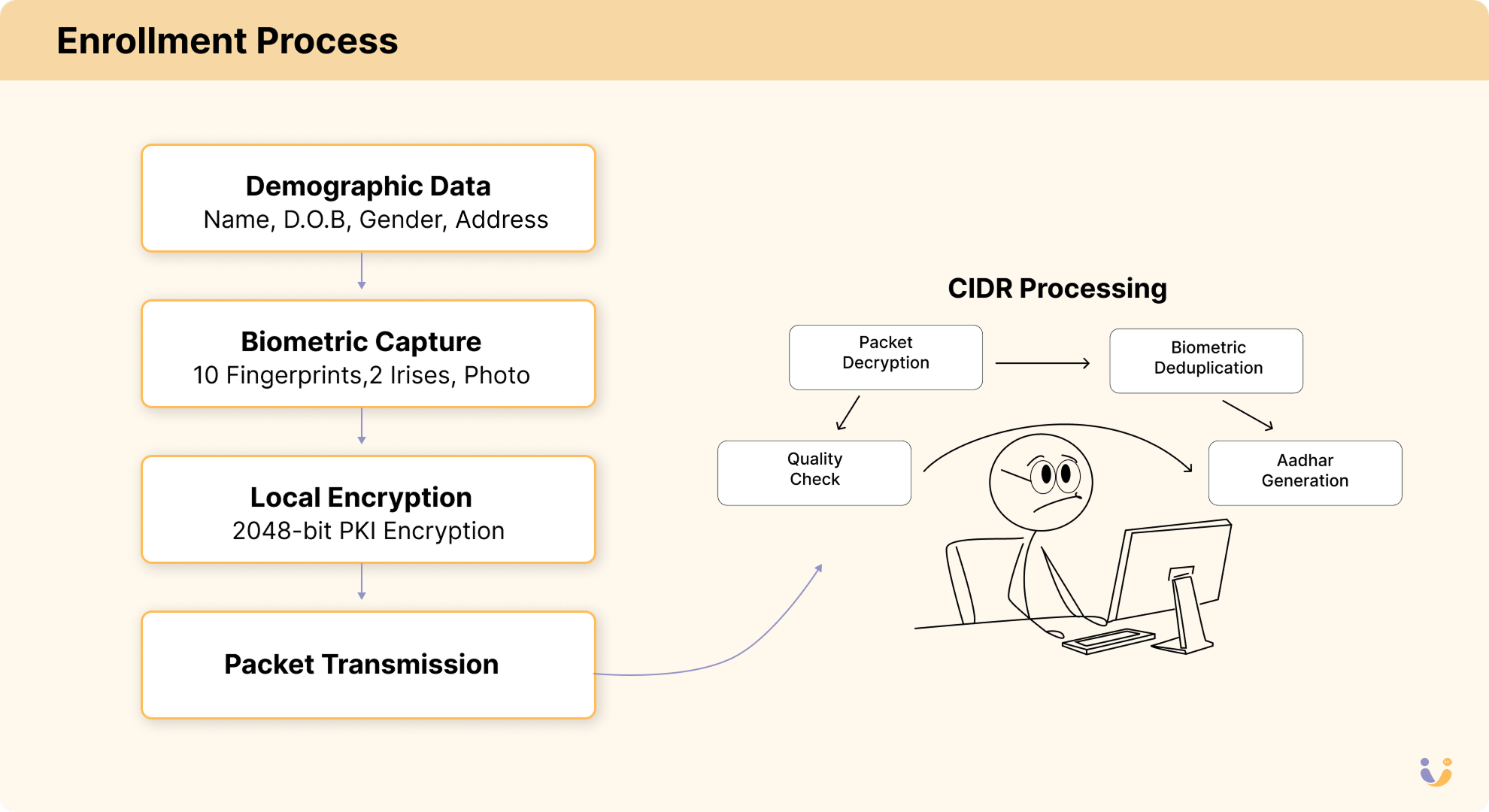
The enrollment system might be the most impressive data pipeline ever built. Think about it — you need to:
- Capture high-quality biometrics from people who may have never used a computer
- Transmit that data securely from remote villages with spotty connections
- Validate the quality of fingerprints, iris scans, and photos
- Check for duplicates against a database that would eventually hold 1.3+ billion entries
- Generate and issue a unique 12-digit number
- Deliver credentials to the correct person
All while maintaining a throughput of millions of enrollments per day.
The enrollment stations themselves were engineering marvels — custom ruggedized hardware with specialized biometric scanners that had to work in environments from the humid coastal regions to dusty deserts. The software needed to run with minimal resources but still perform sophisticated quality checks on biometric data.
Here's where they got clever: Instead of trying to build one massive system, they created a decentralized enrollment architecture. They empowered multiple registrars (both government agencies and private entities) to conduct enrollments using standardized, certified equipment and software.
Each enrollment generated a 5-10 MB packet of encrypted data containing:
- Demographic data (name, gender, date of birth, address)
- Biometric data (10 fingerprints, iris scans from both eyes, facial photograph)
- Supporting documents (scanned)
- Metadata about the enrollment process
These packets were then transmitted (sometimes physically transported on hard drives from areas with no connectivity!) to the central processing system.
The Deduplication Challenge: Finding Needles in a Billion-Person Haystack
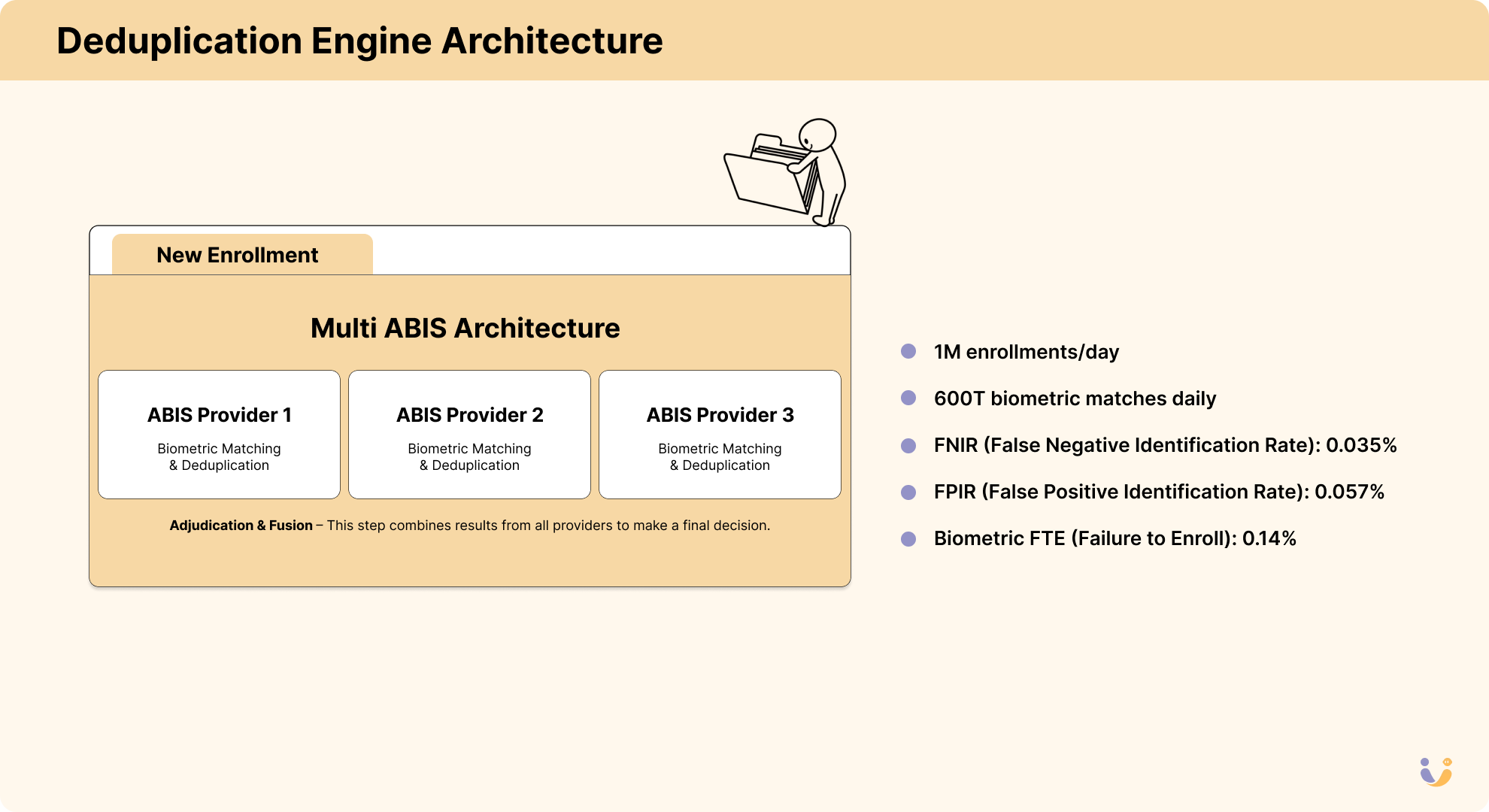
Now we get to the real computational beast: deduplication.
Each new enrollment needed to be checked against every existing record to ensure no duplicates. As the database grew, this became a truly massive computational problem.
Let's do the math:
- Each new enrollment = checking against 1.3 billion existing records
- Each check compares multiple biometrics (10 fingerprints, 2 iris scans)
- Required accuracy: 99.999%
- Required throughput: millions per day
This is where the UIDAI made a brilliant architectural decision. Rather than relying on a single vendor or algorithm, they deployed a multi-modal, multi-vendor approach:
They built an Automated Biometric Identification System (ABIS) that used multiple biometric matching algorithms from different vendors working in parallel. This created both redundancy and improved accuracy through ensemble methods.
The system would:
- Perform 1:N matching of each fingerprint and iris against the entire database
- Calculate matching scores using multiple algorithms
- Use fusion algorithms to combine these scores
- Flag potential duplicates for human review
The computing infrastructure required was staggering:
- Hundreds of thousands of CPU cores
- Specialized biometric matching accelerators
- Petabytes of storage
- Custom-built high-throughput networking
And remember, this wasn't a one-time batch job. This system needed to run continuously as new enrollments came in, with response times measured in hours, not days or weeks.
CIDR: The Database at the Center of It All
The Central Identities Data Repository (CIDR) is one of the most secure and highly available database systems ever built. It needs to be — it holds the biometric data of over 1.4 billion people.
The architecture follows a multi-tier design:
- Storage Layer - Highly distributed, encrypted database containing biometric and demographic data
- Service Layer - APIs and services for enrollment, updates, and authentication
- Application Layer - Business logic for identity management
- Presentation Layer - Interfaces for administrators and authorized users
But the real magic is in how they designed for scale, security, and availability:
Partitioning Strategy: The database is partitioned both vertically (separating biometric and demographic data) and horizontally (sharding by geographic regions and other factors). This allows for both security isolation and performance optimization.
Replication and Redundancy: Multiple data centers across different geographic zones with real-time replication, ensuring no single point of failure could bring down the system.
Encryption Everywhere: All data at rest and in transit is encrypted. Biometric data has additional layers of encryption with strict access controls.
Immutable Audit Logs: Every transaction, query, and data access is logged in immutable audit trails, ensuring accountability and forensic capabilities.
The scale is mind-boggling:
- Petabytes of highly sensitive data
- Billions of database transactions daily
- Sub-second response times for authentication
- 99.99% uptime requirements
The Authentication System: Making Identity Useful
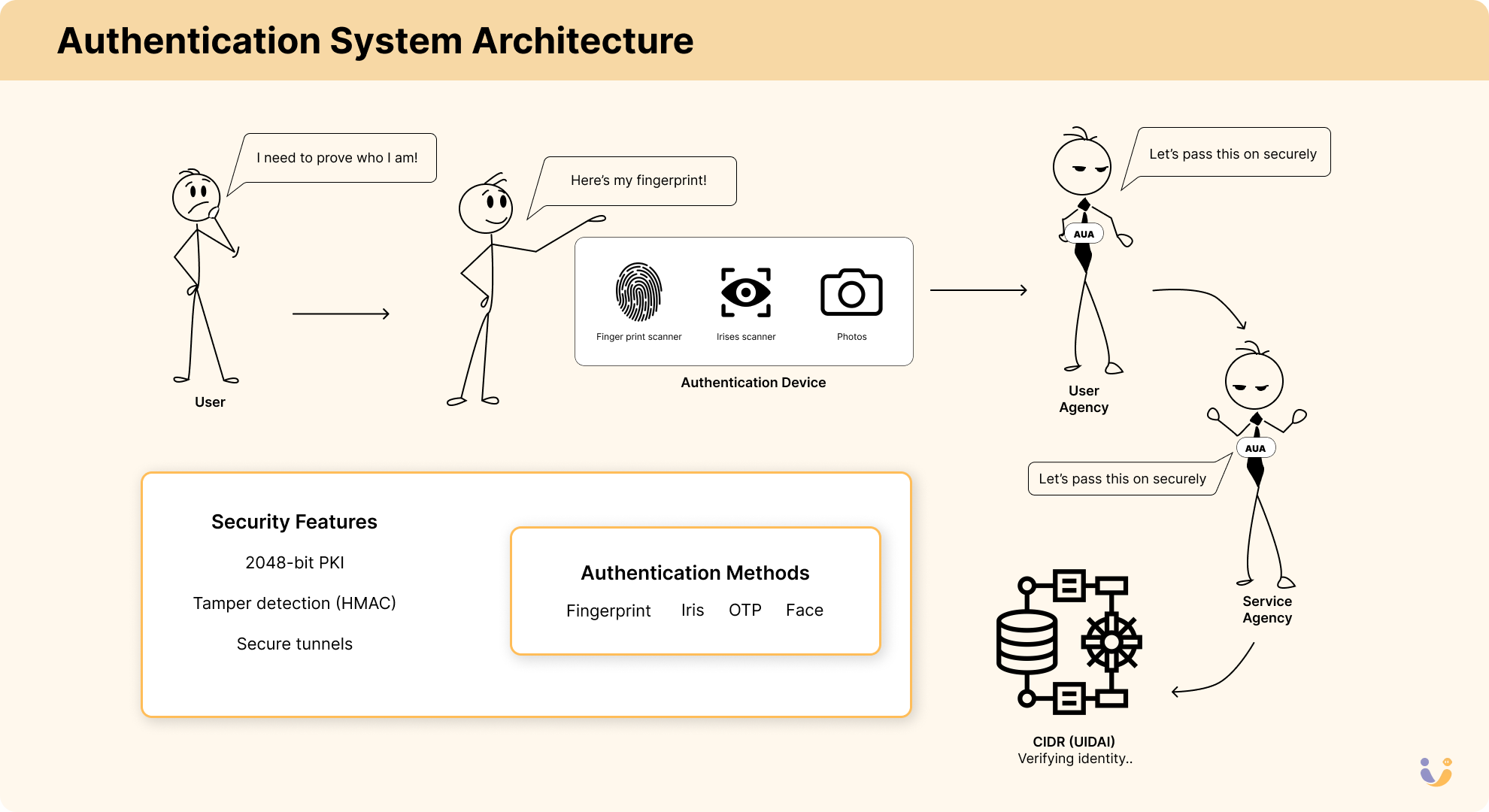
Having a database of identities is one thing. Making it useful in the real world — often in remote areas with limited connectivity — is another challenge entirely.
Aadhaar's authentication system is what brings the value. It allows any authorized entity to verify a person's identity in real-time through a simple API. The system supports multiple authentication factors:
- Demographic authentication - Verifying name, gender, date of birth, address
- Biometric authentication - Fingerprint, iris, or face matching
- One-time password (OTP) - Sent to a registered mobile number or email
The authentication workflow is brilliantly designed for both security and scale:
- An authentication request comes in through a registered Authentication User Agency (AUA)
- The request is encrypted and contains the Aadhaar number and the biometric/demographic data to verify
- The CIDR matches the provided data against stored records
- A yes/no response is returned (not the actual data, preserving privacy)
- The entire transaction is logged for audit purposes
The authentication system handles over 246 million authentications daily, with spikes going much higher. The response time SLA is typically under 500ms, regardless of load.
What's brilliant here is the privacy-preserving design. The authentication system only returns a "yes" or "no" — it doesn't share the actual biometric or demographic data. This minimizes privacy concerns while still providing utility.
Scaling Challenges and Solutions
Building Aadhaar wasn't just a technical challenge — it was an exercise in scaling on multiple dimensions simultaneously.
Technical Scaling
Database Growth: As enrollments increased, the database grew to petabyte scale. The team implemented advanced partitioning, indexing, and caching strategies to maintain performance.
Authentication Traffic: Authentication requests grew exponentially as more services integrated with Aadhaar. They built a highly distributed authentication architecture with intelligent load balancing and regional processing centers.
Network Bandwidth: Many remote enrollment centers had limited connectivity. The solution included store-and-forward mechanisms, data compression, and bandwidth-efficient protocols.
Operational Scaling
Enrollment Centers: Scaled from hundreds to hundreds of thousands of enrollment centers across the country.
Training: Had to train over 400,000 enrollment operators in biometric capture techniques.
Hardware Logistics: Deploying, maintaining, and replacing specialized biometric hardware across a subcontinent.
Security Scaling
Threat Surface: As Aadhaar became more central to India's infrastructure, it became a bigger target.
Response Teams: Built 24/7 security operations centers with automated threat detection.
Encryption Management: Managing encryption keys and certificates at massive scale without compromising security.
The Tradeoffs: Nothing at This Scale Comes Without Compromise
No system of this scale is without tradeoffs, and Aadhaar has faced its share of criticism and challenges:
Privacy vs. Utility: More authentication uses means more potential privacy risks. Aadhaar has constantly balanced providing utility against protecting privacy.
Security vs. Accessibility: Stronger security often means more complexity, which can exclude less technically savvy users.
Centralization vs. Resilience: A centralized identity system provides efficiency but creates systemic risks if compromised.
Mandatory vs. Voluntary: Originally voluntary, Aadhaar became effectively mandatory for many services, raising legal and ethical questions.
The system has evolved in response to these challenges. Court rulings have limited mandatory usage in some contexts, and security measures have been strengthened over time.
The Technical Lessons: What Can We Learn?
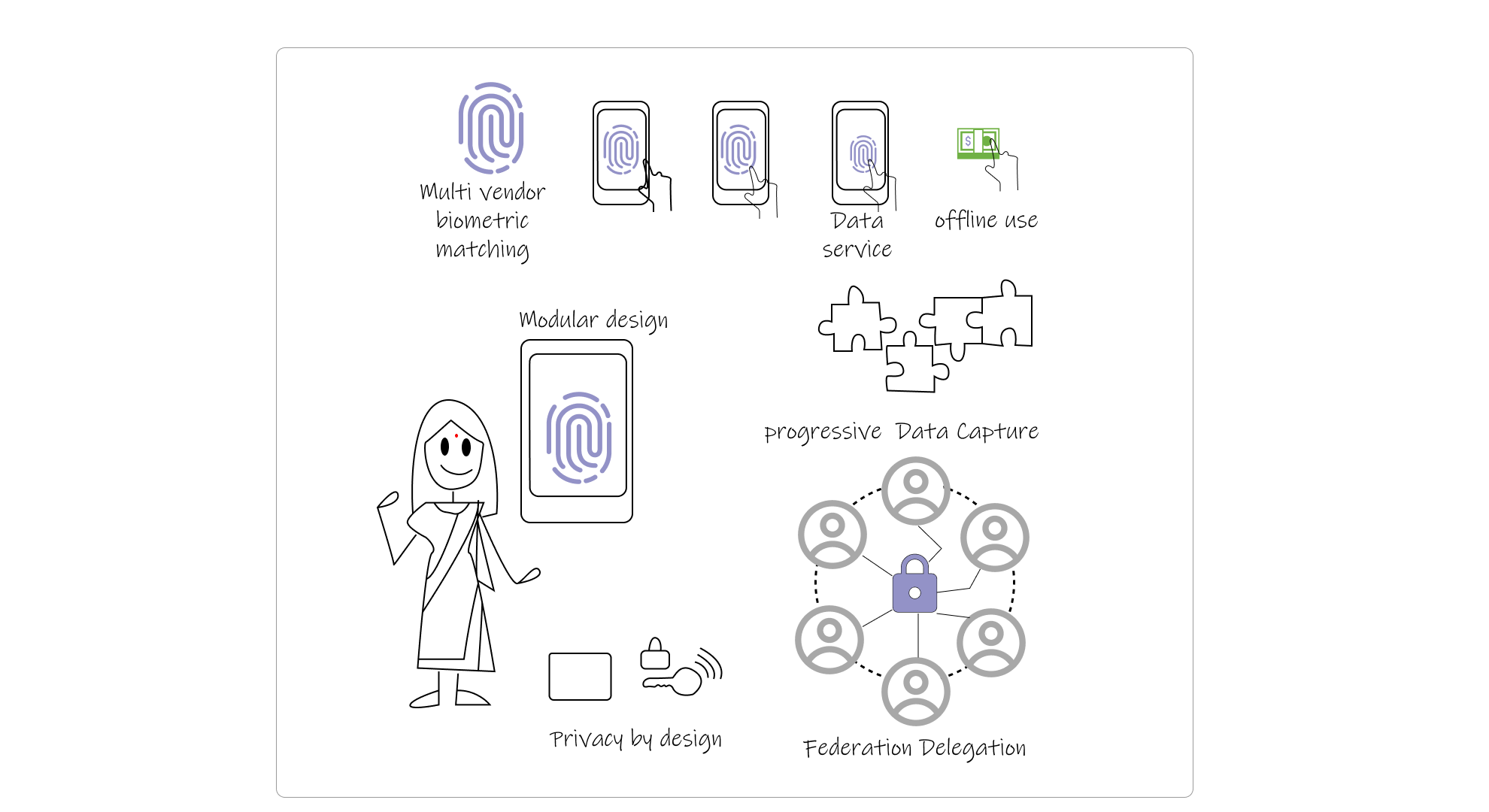
Aadhaar offers incredible lessons for anyone building large-scale systems:
- Multi-vendor biometric matching: By using multiple biometric matching algorithms from different vendors, Aadhaar avoided single points of failure and improved accuracy. This competitive approach among ABIS (Automated Biometric Identification System) providers has ensured continuous improvement in throughput and accuracy while preventing vendor lock-in.
- Design for offline use from the beginning: Many authentication scenarios needed to work with intermittent connectivity, so offline capabilities were built in from the start.
- Modular architecture enables evolution: The system has evolved significantly since launch, adding new features and security measures without disrupting core functionality.
- Progressive data capture works better than big bang: Aadhaar started with basic identity data and gradually expanded to include more information, allowing for faster initial deployment.
- Privacy by design is essential: The yes/no authentication model and the separation of authentication from data sharing has been crucial to Aadhaar's acceptance.
- Federation and delegation enable scale: By creating a network of registrars and authentication agencies, Aadhaar achieved geographic and operational scale impossible for a single entity.
Beyond Identity: The Platform Effect
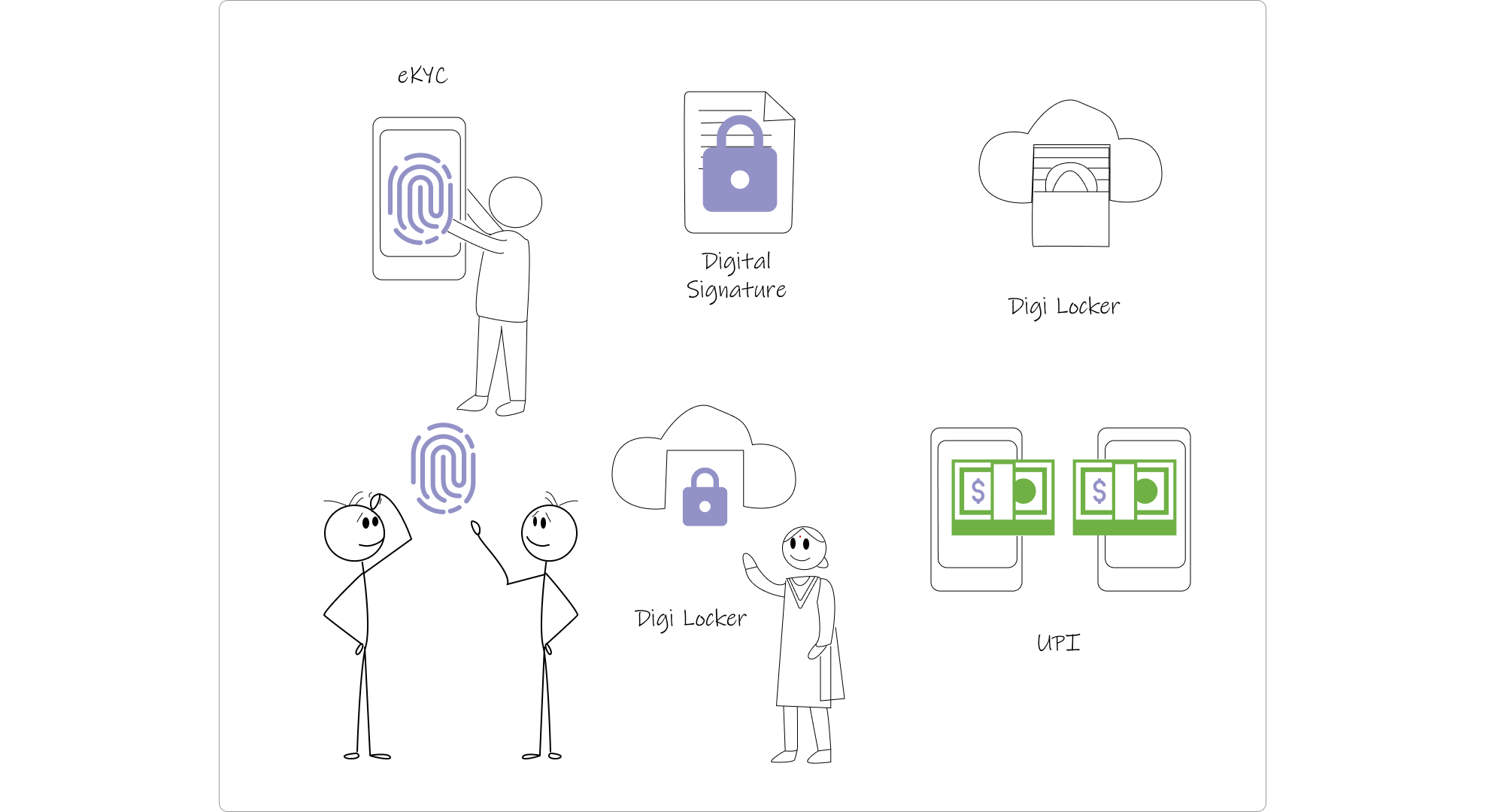
The most fascinating aspect of Aadhaar isn't just the identity system itself — it's what it enabled.
On top of Aadhaar, India built the "India Stack" — a set of open APIs and digital public infrastructure that includes:
- eKYC: Electronic Know Your Customer verification
- Digital Signatures: Legally valid paperless signatures
- DigiLocker: Digital document repository
- UPI: Unified Payments Interface, a real-time payment system
This platform approach has transformed India's digital landscape. The volume is staggering:
- UPI processes over 9 billion transactions monthly
- DigiLocker holds over 5 billion documents
- eKYC has dramatically reduced onboarding costs across industries
The Numbers That Tell the Story
Let's put some final numbers on this achievement:
- 1.4 billion+ people enrolled
- Over 150 billion authentication transactions performed since launch
- 99% of adults in India covered
- 250+ million duplicates and fakes eliminated from welfare rolls
- $40+ billion saved in government benefits through reduced leakage
- High success rate for fingerprint authentication, with face authentication growing rapidly
What's Next: The Future of Digital Identity
Aadhaar has become a case study for digital identity systems worldwide. Other countries are now looking to implement similar systems, learning from both its successes and challenges.
The future evolution might include:
- Self-sovereign identity models: Giving users more control over their identity data
- Blockchain-based verification: Adding additional transparency and decentralization
- Advanced liveness detection: Countering increasingly sophisticated spoofing attempts
- Cross-border identity interoperability: Creating standards for international identity verification
Final Thoughts: When Engineering Meets Society
Building Aadhaar wasn't just a technical challenge — it was a social transformation project wrapped in a technical shell. The system has dramatically reduced fraud, increased financial inclusion, and created a platform for digital innovation.
By directly transferring subsidies to bank accounts through the Direct Benefit Transfer (DBT) program, the government has saved approximately $40 billion by eliminating fake beneficiaries and middlemen from welfare schemes.
But it also reminds us that when we build at this scale, we're not just engineering systems — we're reshaping societies. The responsibility that comes with that is immense.
The next time you're designing a system and feeling proud of your 99.99% success rate, remember: at true scale, that final 0.01% can affect millions of real people. That's the mindset that Aadhaar's builders had to adopt, and it's one worth carrying into any large-scale system design.
Because when you're building for a billion people, 99.99% just isn't good enough.
